When there’s a breach in IT, you can typically shut down or isolate the breached systems while you take appropriate remedial action and restore from backups. Yes, it still causes pain and financial impact to the business, but no one gets physically hurt.
In the OT and ICS world, cybersecurity breaches become a safety issue - and in extreme cases put lives at risk - because these systems are controlling physical equipment and safety systems. Uncontrolled changes to this equipment can cause explosions, or damage that can take months or years to repair or rebuild.
Even if there are no dangerous outcomes, if your OT or ICS systems can’t function as the result of a hack or breach, most industrial sites can’t be run manually. There are no workarounds or alternatives - nothing gets made or processed until they’re back working. It’s not like the business side where you can buy new computers, restore from backups, connect to the cloud and keep working.
How long can your business keep operating if it can’t actually build or process its core product?
The latest Australian Cyber Security Centre Threat Report stats also confirm what we all know – the cybersecurity problem just keeps growing.
- 67,500 reported cybercrimes and cyber-attacks during FY20/21 in Australia
- This equates to one cyberattack approximately every 8 minutes
- 13% overall increase in cyberattacks
- 15% rise in ransomware attacks
- 54% increase in financial losses from the attacks during FY20/21 compared to the previous period
- Self-reported losses from cyber-crime in Australia are approximately $33 billion.
This means we need different thinking, skillsets and solutions to protect OT and ICS environments.
Why do OT and ICS need different solutions?
The IT-centric view is that all these systems are still connected to computer networks which are subject to the same protections and processes that corporate systems have. But let’s look at a couple of examples that highlight the challenges faced in OT and ICS environments.
- Keeping computer systems patched and up to date is often touted as a fundamental activity in keeping them secure. However, what do you do when the proprietary software that manages a series of pumps only works on an old version of Windows that is no longer supported or patched? You could have millions of dollars of industrial equipment reliant on an old Windows PC that can’t be upgraded or updated because the software hasn’t been updated to run on newer equipment.
- Managing and regularly changing passwords on systems is a big focus, but with ICS, the nature of the day-to-day operations mean that you either have shared logins or no login at all. If an operator needs to quickly act in a control room, the last thing you need for them is to be fumbling around trying to remember a username and password. With multiple operators across multiple shifts often doing similar things, these systems assume that once you’re in, you’re authorised to do everything.
These are just 2 simple examples of how the different operating environments of OT and ICS make traditional cybersecurity approaches less effective, but the cybersecurity priorities in these environments are also different.
The classic CIA triad that guides policies for information security covers Confidentiality, Integrity and Availability, but it prioritises confidentiality and integrity first and foremost. Personal data breaches are a huge problem and for most cybersecurity vendors that’s how their solutions are aligned and sold.
For OT and ICS though, availability is the clear priority, not confidentiality and integrity. You need your industrial equipment operational whereas the data you’re collecting off sensors, pumps, systems etc is hardly confidential. While this seems like a subtle shift, it does have an impact on the solutions you choose.
How should companies approach OT and ICS security?
While every environment obviously has a lot of differences, there are best practices we’ve identified over the years that organisations need to be aware of, using a classic stop doing, keep doing and start doing classification. This is a generalised list, and, in your environment, you might already be doing something we’ve labelled as “Start Doing”, however, we feel this list still serves as a useful checkpoint.
Stop Doing:
- Treating your IT and OT/ICS environments the same when it comes to cybersecurity. While there are linkages between the two, they need different thinking and different approaches as we’ve outlined above. Adding additional stakeholders to IT cybersecurity teams that can represent your OT/ICS environments is a good start.
- Underestimating the risk and financial consequences of a breach in your OT/ICS environment, compared to your corporate environment. Just focusing on physical security measures to protect these environments isn’t enough and the costs of a breach that seriously affects your production can cost many times more than a corporate systems breach.
Keep Doing:
- Mandating separation of systems both physically and digitally. Most organisations we see have some level of separation implemented, although it tends to focus more on the physical side with site access controls, security guards, secure access control rooms etc. This includes differentiating and separating vital and non-vital systems so, for example, your computer surveillance systems aren’t on the same network as your ICS, and no ICS system can be accessed from the corporate network.
- Related to the above point - ensuring no OT/ICS computer is connected to the internet or has shared access to applications like email. It sounds obvious, but we’ve seen many examples where a computer in the control room is used for email as well as ICS.
- Maintaining separate identity systems between your corporate network and your OT/ICS network so that a breach in credentials on one side doesn’t automatically provide access to the other. The Colonial Pipeline hack in the US is the perfect example of the need for this, although after reading the reports it seems like the team didn’t actually know if this separation existed and had to take actions that assumed the worst.
Start Doing
- Problems with OT and ICS security often stem from a lack of clarity on who is responsible leading to finger-pointing and “I thought Bob was looking after that” type of discussions. In your cybersecurity governance documentation, clearly identify the team and the roles that are responsible for approving and maintaining OT and ICS cybersecurity initiatives.
- Training your operations staff on cybersecurity awareness. This gets done on the corporate side of the business, but operational staff seem to get left out. These staff can still click on a dodgy email, visit a malicious website, or have their credentials compromised. They need to be aware of the impacts these actions can still have in an operational environment.
- Application whitelisting on all OT and ICS computer equipment. This means only the essential applications needed to control equipment can be run on these computers and everything else is blocked.
- Extending any penetration testing that is being done on your corporate networks to your OT and ICS networks.
- Implementing proactive asset management and network documentation. As systems evolve and staff change, updating the documentation can easily be forgotten. You can quickly find yourself with no one who actually knows how the environment is configured or what equipment is installed, and you can’t protect what you don’t know about. Ensure there is a well-defined change management documentation process with clear ownership to keep things updated.
Conclusion
This post represents the tip of the iceberg when it comes to OT and ICS cyber security. With the continued digitisation of industrial equipment and systems, they have become increasingly vulnerable to attack. The question for most organisations though is “how much risk is there?” with the answers often being understated.
Assuming your existing IT cybersecurity approaches are working in your OT and ICS environments is a dangerous assumption. You need to clearly understand the current levels of protection and risk so that appropriate actions can be taken.
Our OT cybersecurity team can perform an extensive OT and ICS environment risk assessment giving you the clarity you need on where you currently stand and where you need to be. For more information visit www.denver.com.au or contact us directly to discuss your needs.
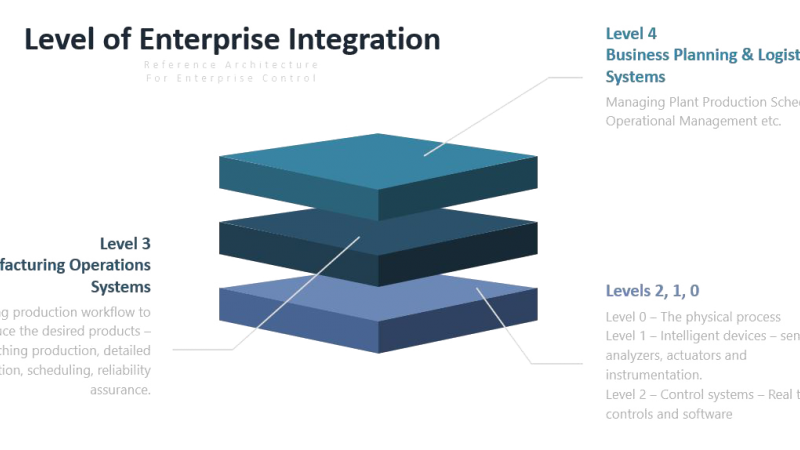
The Critical Need for Secure PCN in Mining, Oil & Gas
Process Control Networks are complex in design and implementation because they integrate with a range of corporate and industrial components. PCN's perform sensitive and vital tasks for managing and handling critical infrastructure. It’s imperative to implement security in these systems because they are targets for cyber-attacks.

The Digital Chemistry between Strategies, Tactics & Operations
Denver’s Digital Maturity Assessment (DMA) Case Study for a Major Chemical Manufacturer in The Mining Industry.
